Have you ever needed to locate and replace encrypted secrets in your Splunk configurations? It’s a tricky task that requires careful handling. In this article, we’ll guide you through the process.
Introduction
Finding encrypted secrets in Splunk configurations can be essential for various reasons. Replacing the splunk.secret file on a Splunk instance, for instance, requires identifying all secrets encrypted using this file and replacing them with their plain text counterparts. However, it’s crucial to proceed with caution, as mishandling this process can result in significant issues.
Here is a Hurricane Labs article that lays out this process in detail.
Warning: Before proceeding, it’s crucial to understand the potential risks involved in replacing encrypted secrets within your Splunk configurations. Any missteps can lead to significant issues.
Note: If you decide to replace encrypted secrets while Splunk is running, be prepared to recheck for encrypted values once Splunk is stopped, as it may attempt to re-encrypt specific secrets during shutdown.
Linux Commands
Finding Encrypted Passwords on Linux
To find encrypted secrets on a Linux-based Splunk instance, you can use the following command (This is a slightly modified version of the command found in the Hurricane Labs article):
find /opt/splunk/etc -name '*.conf' -not -name 'transforms.conf' -exec grep -inH '\$[0-9]\$' {} \;

Expanded Linux Command
If you also want to view the decrypted values, use this expanded command:
find /opt/splunk/etc -name '*.conf' -not -name 'transforms.conf' -exec grep -inH '\$[0-9]\$' {} \; | while IFS=: read -r file line; do
encrypted_value=$(echo "$line" | grep -oP '\$[0-9]\$[^\s]+')
if [ -n "$encrypted_value" ]; then
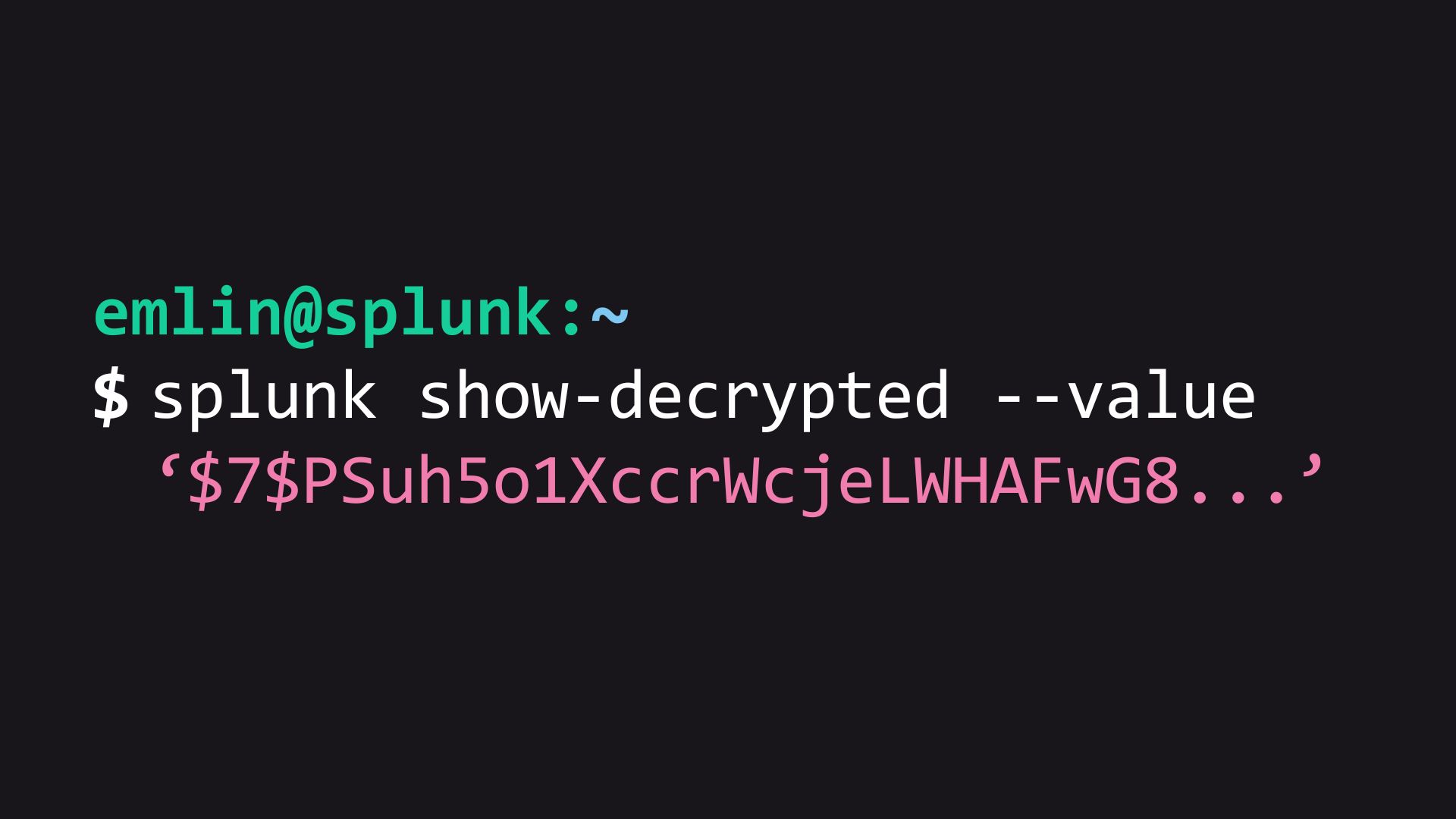
decrypted_value=$(/opt/splunk/bin/splunk show-decrypted --value "$encrypted_value")
echo "$file:$line (Decrypted: $decrypted_value)"
fi
done

Windows Commands
Finding Encrypted Passwords on Windows
For Windows-based Splunk instances, you can use the following PowerShell command to find encrypted secrets:
Get-ChildItem -Path 'C:\Program Files\Splunk\etc' -Filter '*.conf' -File -Recurse | Where-Object { $_.Name -ne 'transforms.conf' } | ForEach-Object { Select-String -Pattern '\$[0-9]\$' -Path $_.FullName -AllMatches | ForEach-Object { Write-Host "File: $($_.Path), Line $($_.LineNumber): $($_.Line)" } }

Expanded Windows Command
If you want to see the decrypted values as well, use this expanded PowerShell command:
$baseDir = 'C:\Program Files\Splunk\etc'
Get-ChildItem -Path $baseDir -Filter '*.conf' -File -Recurse | Where-Object { $_.Name -ne 'transforms.conf' } | ForEach-Object {
$file = $_.FullName
$content = Get-Content -Path $file
$content | ForEach-Object {
if ($_ -match '\$[0-9]\$[^\s]+') {
$encryptedValue = $matches[0]
Write-Host "$encryptedValue"
$decryptedValue = & "C:\Program Files\Splunk\bin\splunk.exe" show-decrypted --value ''$encryptedValue'' 2>$null
if ($decryptedValue) {
Write-Host "File: $file, Line $($_.ReadCount): $_ (Decrypted: $decryptedValue)"
}
}
}
}

Conclusion
In this article, we’ve explored how to find encrypted secrets in Splunk configurations, both on Linux and Windows systems. It’s essential to approach this task with caution, as mismanaging encrypted secrets can lead to potential issues within your Splunk environment.
Happy building! 🙂